Introduction to Win 7 Antivirus 2010: When you are surfing the net peacefully or doing work online, suddenly your PC goes blue screen without any hints. You may experience this a lot. It happens due to Win 7 Antivirus 2010.
When your Windows 7/ XP/ Vista detects an unknown error which make your operating system running inappropriately, your PC will encounter problems and go to blue screen immediately. You may get words or messages from the screen which is reading: ***STOP 0×0000001E(0xC0000005,0xFDE38AF9,0×0000001,0×7E8B0EB4). This is Win 7 Antivirus 2010 error.
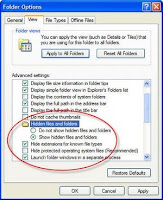
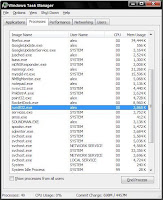
Removal of Win 7 Antivirus 2010
1. There is BUG existing in your applications. As mentioned before, BUG or errors on your operating system can make it run improperly and go to blue screen finally. You should clear or fix virus completely.
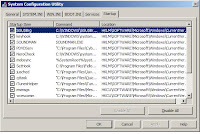
2. You are loading too many programs while booting up your PC. Some users may get the Win 7 antivirus 2010 whenever they boot up computer. Too many programs added into Startup will not only slow down the booting speed, but also enhance the possibility of getting Win 7 antivirus 2010. Reduce the unnecessary items in Startup to make it run faster.
3. Incompatibility of software and hardware on your PC also may cause the Win 7 antivirus 2010 problem. When you install software or change hardware, you need to think about the compatibility of them and then make the decision.
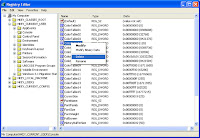
4. Registry encounters problem or has been destroyed. Registry is a huge database including all the configuration information of all applications on your computer. Once it starts to show errors, you need to get some repair tool to fix Win 7 antivirus 2010 soon.
5. Win 7 antivirus 2010infection is also one of the main reasons. When your computer is attacked by unknown virus or malicious threats, it is easily to freeze or become blue screen. Moreover, it is extremely hard for common users to detect and remove the virus completely. You had better get a professional tool to fix Win 7 antivirus 2010 instantly.